Sign up and log in
Create your account and access the platform immediately. No complex setup, no integrations to configure, no training required.
Your first 25 projects are on us. Start delivering value to clients from day one and only purchase slots when you're ready to scale.
- 25 free projects to prove value with real clients
- Full platform access - all features unlocked
- CIH Concierge - AI assistant to guide you
- White-label reports - your branding, our intelligence
Add your clients
Click "Add Client" and enter their domain. That's it. CIH immediately begins discovering assets and preparing to scan threat intelligence sources.
No agents to install. No API keys to configure. Just a domain name and you're ready to launch.
- Primary domain: acmecorp.com
- Additional domains: (optional) acme-corp.net
- Keywords: (optional) company name variations
CIH automatically discovers subdomains, email patterns, and related infrastructure.
Launch assessment or continuous monitoring
Choose how you want to serve this client. Assessment mode for one-time projects, continuous mode for ongoing managed services.
Mix and match freely across your client base. Use assessments for new business development and continuous monitoring for retainer clients.
- Assessment: 14-day deep scan, slot freed for reuse after
- Continuous: Ongoing monitoring, alerts for new exposures, 3-month minimum then cancel anytime
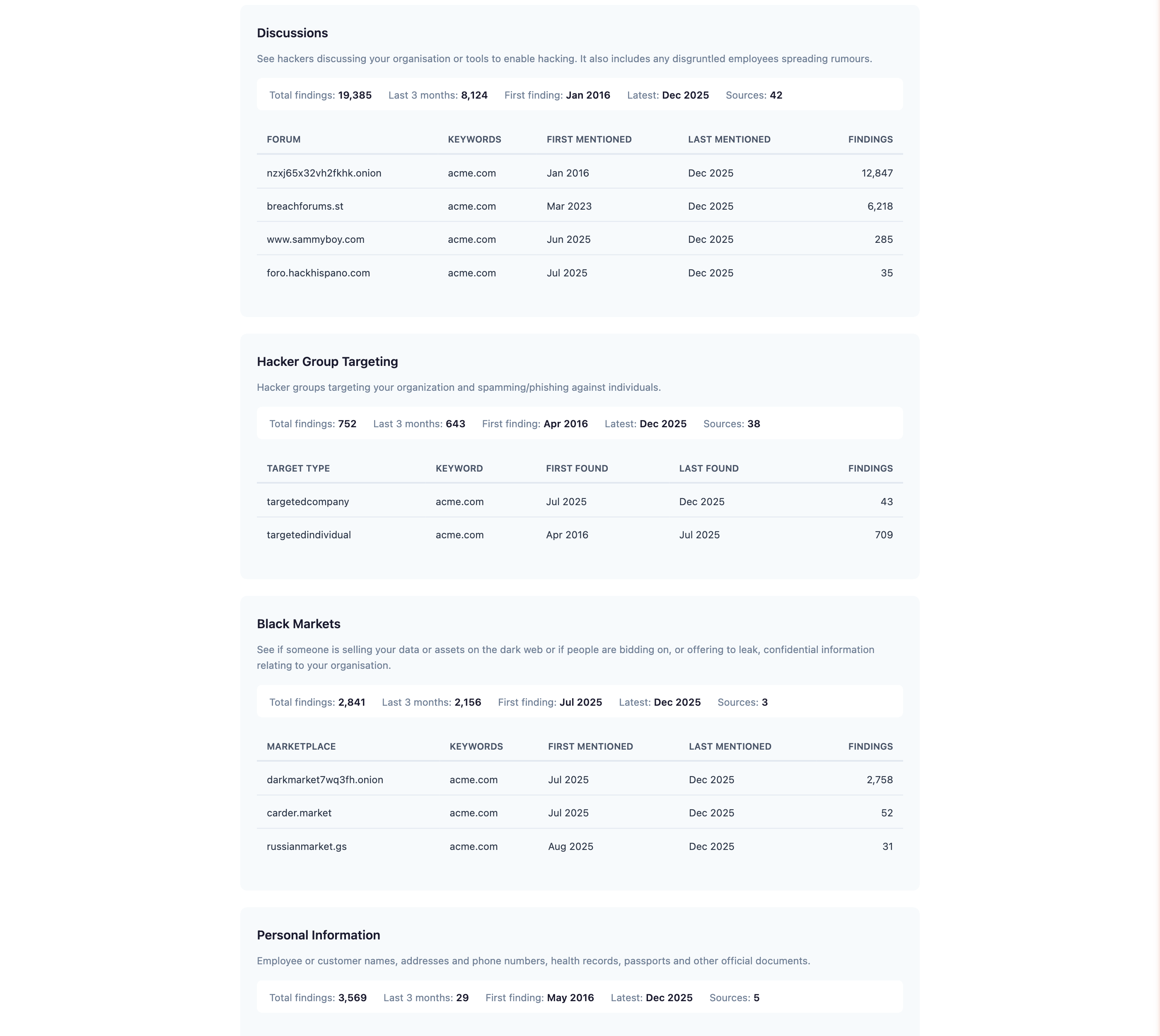
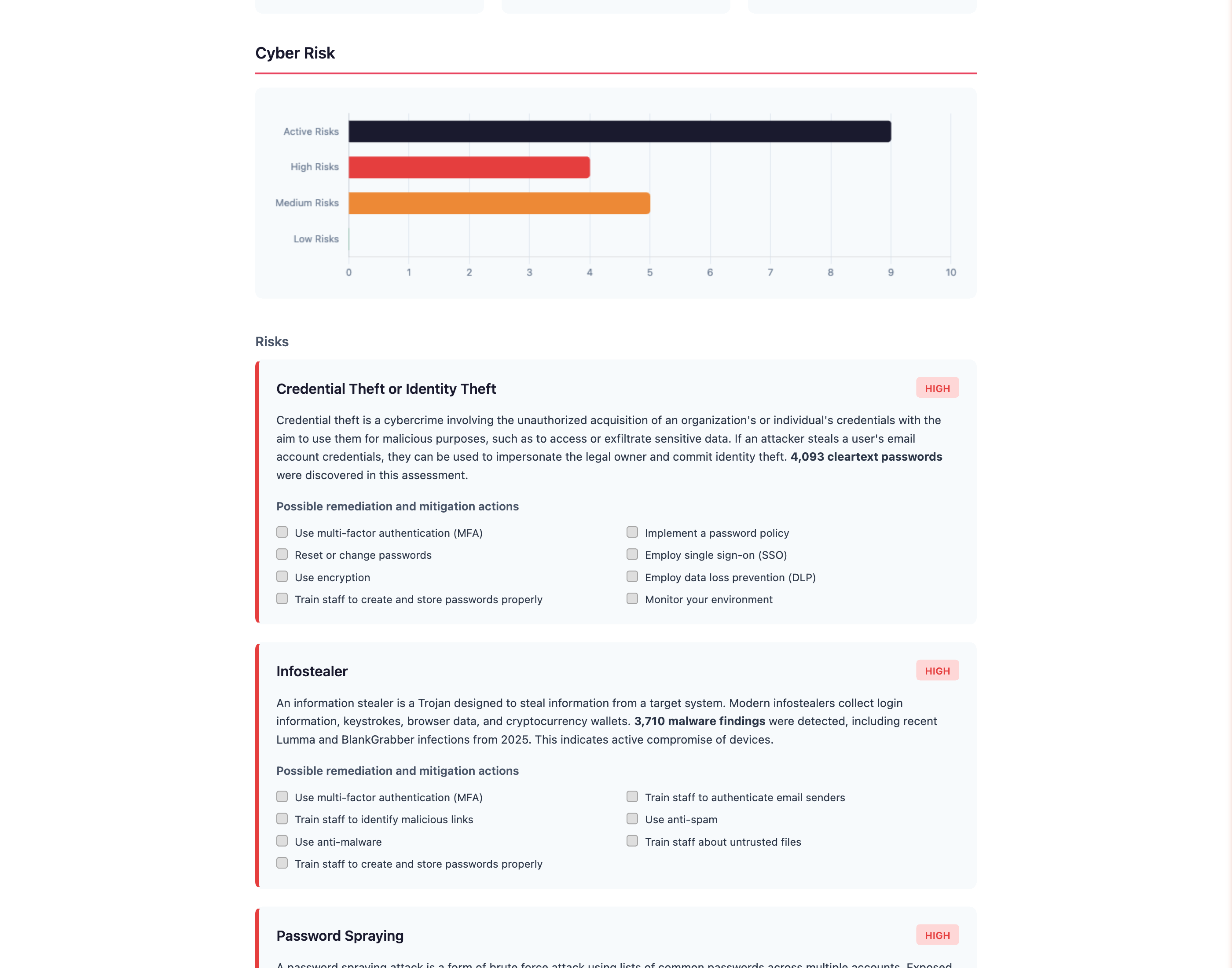
Review findings and ask Concierge
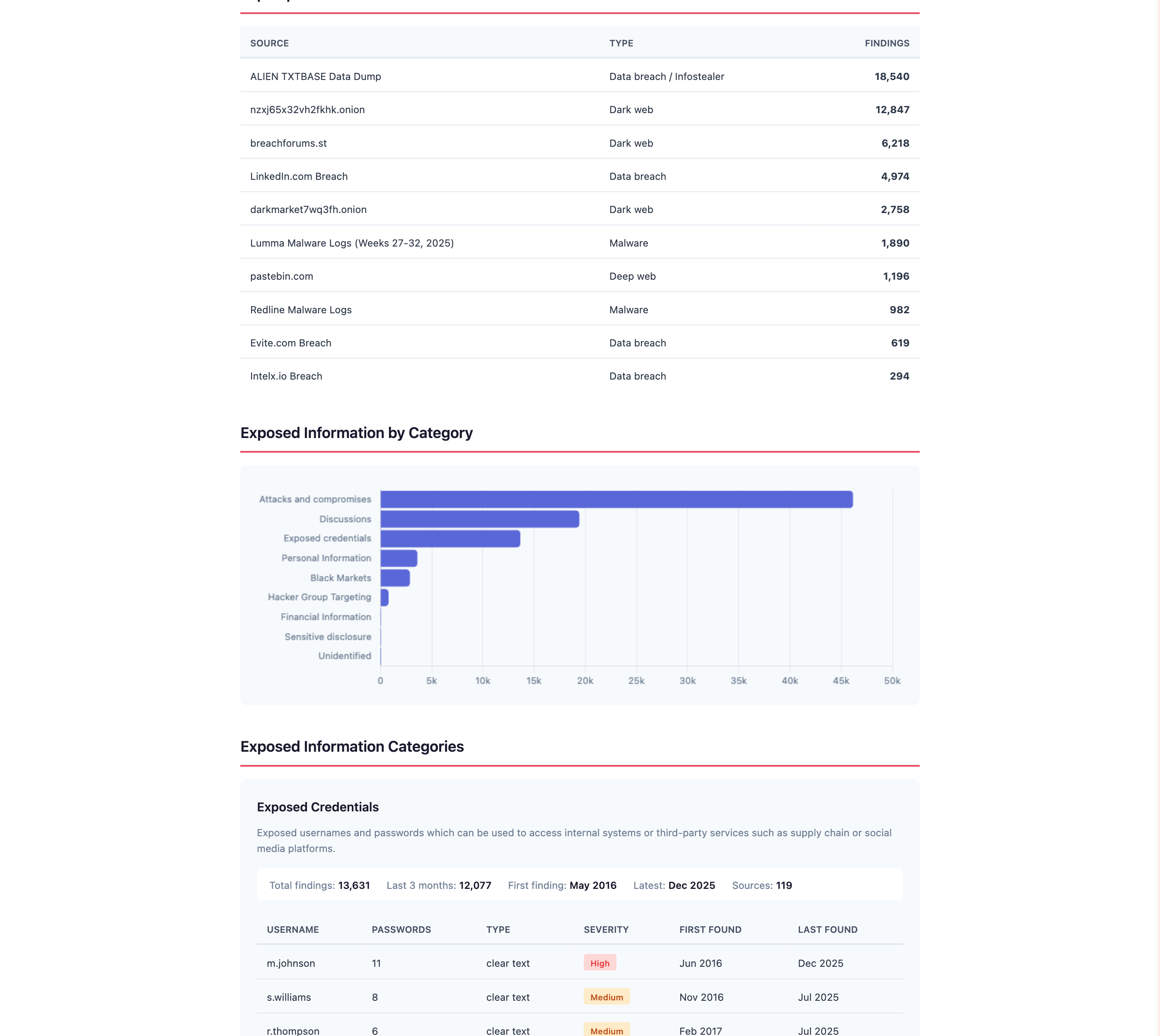
As CIH discovers verified exposures, they appear in your dashboard with full context. Use CIH Concierge to interrogate findings, get remediation guidance, or understand risk.
Every finding is verified before it reaches you. No noise, no false positives. The kind of intelligence that makes clients ask "how did you get this?"
- Leaked credentials: Employee emails with exposed passwords
- Infostealer logs: Devices with saved sessions and cookies
- Dark web mentions: Company data on marketplaces
- Ransomware lists: Appearances on victim announcements
- Hacker chatter: Discussions and targeting mentions in threat actor channels
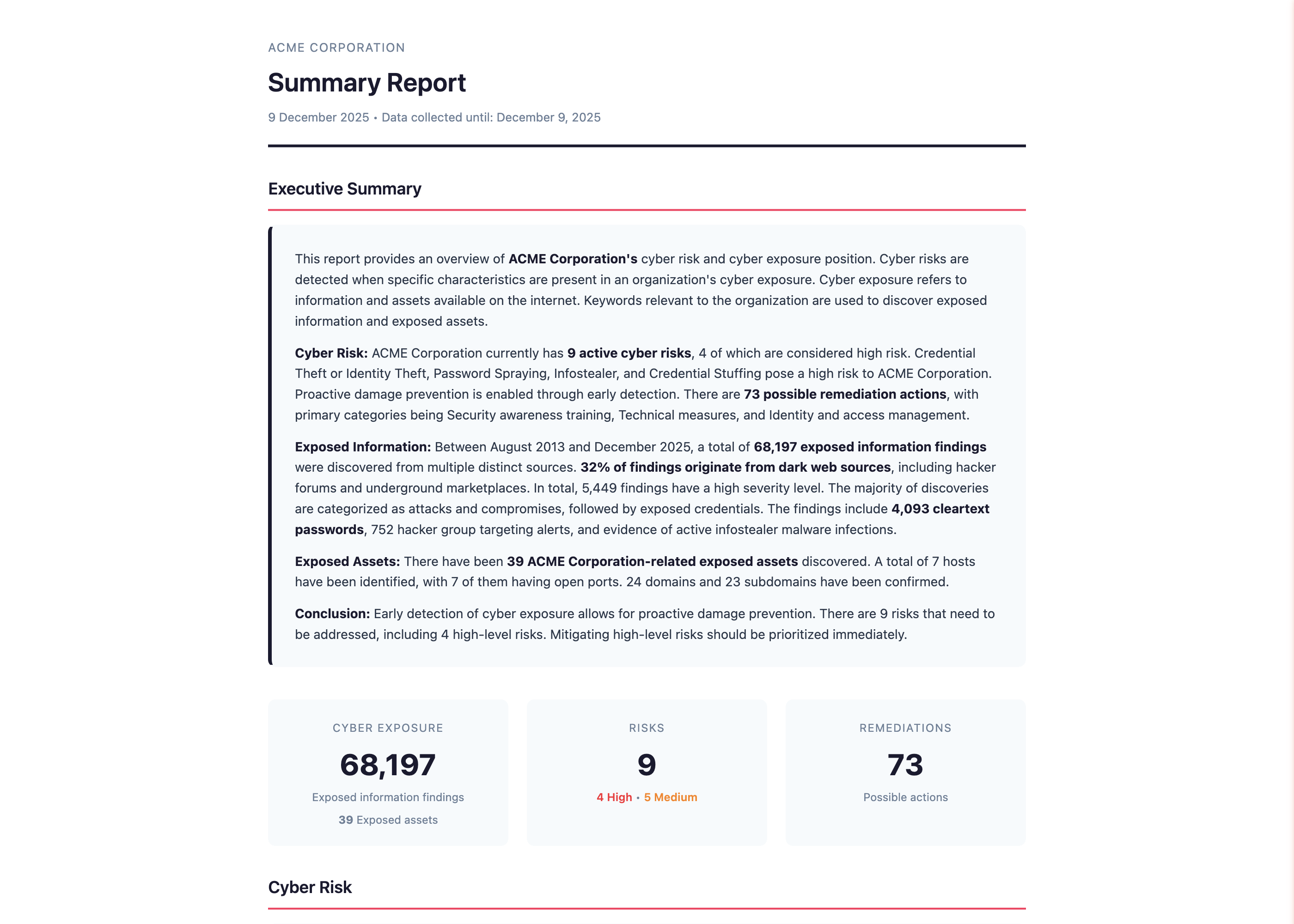
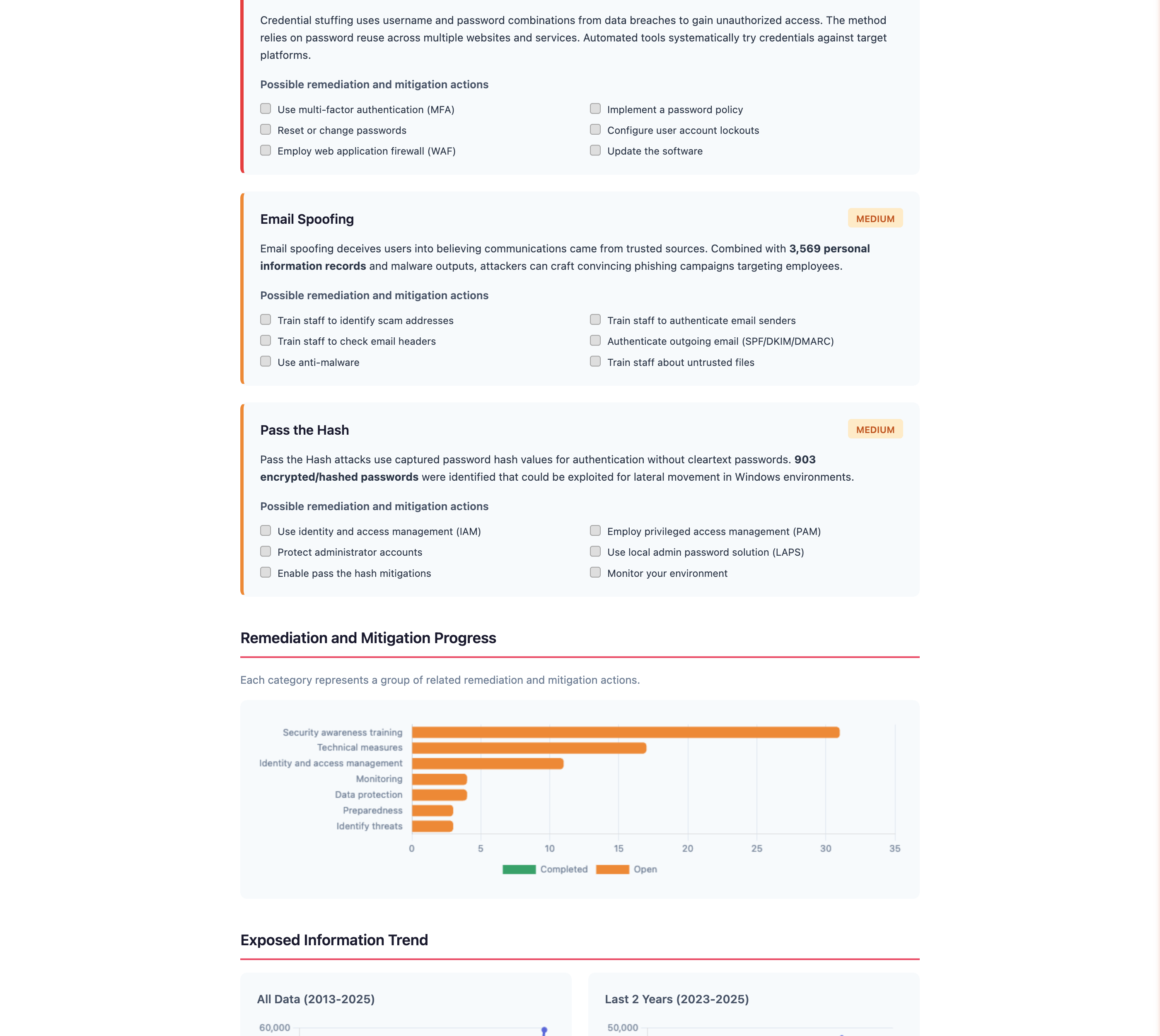
Generate reports and deliver value
Generate professional, white-labeled reports with one click. Each report includes executive summary, detailed findings, evidence, and remediation guidance.
Reports are designed for both executives and technical teams. Your branding, our intelligence. Invoice your client and deliver real security improvements.
Executive Summary:
Assessment identified 62 verified exposures requiring attention, including 47 leaked credentials and evidence of 12 compromised devices.
- Critical: 8 findings requiring immediate action
- High: 19 findings for priority remediation
- Medium: 35 findings for scheduled attention
See the full sample report inside the platform after you sign up.
- Credential reset campaigns for affected employees
- Malware removal from infected endpoints
- Security awareness training recommendations
- Configuration hardening guidance
Every finding is something you can fix. CIH surfaces problems, you deliver solutions.